Access Control Systems
Every building requires an access management system. Whether it’s a garden shed with a padlock and a key, a modern home with an electronic door lock and security system, or a large office tower requiring multi-faceted access solutions, one thing remains the same: Assets and occupants need to be protected while allowing everyday operation the buildings were designed for. Sounds easy, right?
Bosch Access Systems
Different stakeholders want different things from access management. A resident or an employee will want an easy means to access the building, whether it is through the front door, a lift or a garage. A security manager will want to easily manage and restrict access whether they are for employees, visitors, contractors or residents of the building. No matter the building, or the stake owner, a modern access system needs to be scalable, easily manageable, effective against unwanted intruders, easily integrated with security, safety and public address systems, be highly resilient, and operational 24/7. This is where Bosch Access systems have excelled over the last 35 years.



Comprehensive & Scalable
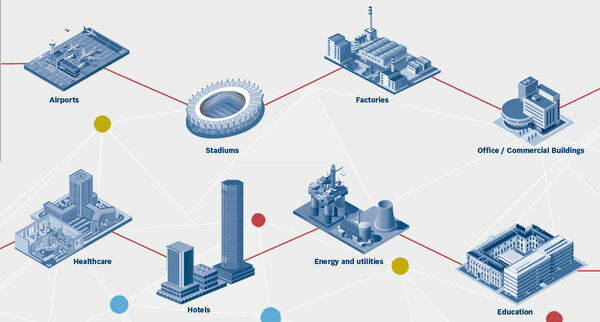
Bosch offer Access Control Systems for applications of any size. Thanks to the scalability of the hardware – access modular controllers, readers and credentials – the system grows with the needs of the project. Access Management System (AMS) is ideal for medium and large-sized projects, such as office building, libraries, shopping centres and hospitals. Up to 10,000 doors and 200,000 card holders are possible.
Scalable Hardware
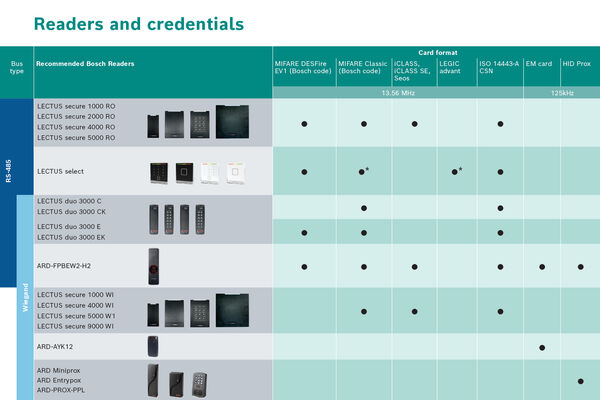
A wide selection of readers is available is available for all levels of security. Bosch offers a wide range of readers and cards, from fully featured advanced solutions to cost-effective starter systems. Most models are available with or without keypad or as biometric versions. Wiegand and RS-485 (OSDPv2 SC) support ensures that our solutions work seamlessly with your technology.
Acces Software
Access Management Software v3 is ideal as standalone and also capable of growing into a complete integrated security solution. It is easy to set up, operate and expand. The software is offered in three pre-configured bundles for different sized organizations: Lite, Plus and Professional. All three versions are fully functional and can be used directly “out-of-the-box”. They can also be enhanced with further expansion licenses when needed. In total, up to 200,000 cardholders and up to 10,000 doors can be administered. Since no hardware needs replacing, increasing the system size is very cost-efficient. The Access Management System v3 can also be integrated with video management systems and G Series intrusion panels.

Operation & Resilience 24/7
Access Management System v3 includes the Master Access Controller (MAC) as an additional layer of resilience between the server and the access controllers. If the server fails in the Access Management System, the MAC takes over and ensures that the controllers still communicate with each other and share necessary information from the card readers. Functionalities which include various controllers such as anti-passback, guard tour and area control can still be performed. To avoid any disruption in the rare event of the workstation and the MAC both failing, a second MAC can be configured as a redundant MAC (R-MAC). This concept provides the customer with the highest system availability.
Integration with video
The Access Management System v3 can be integrated with video management systems such as BVMS (10.1 and higher) and Milestone XProtect. Integration with BVMS offers manual video verification to increase the security level at doors. Here the operator verifies if the person at the door matches the registered person in the database and if so, allows the person to enter. BVMS integration also enables searching for cardholder events and events at doors. With the searching functionality, it is possible to quickly check who has entered this area and at what time. Access commands and events can also be handled in BVMS, making the operation of the integrated system most efficient.
Integration with G Series Panels
G Series Intrusion Panels integrate seamlessly into the Access Management System v3 for efficient authorization management and a central overview of all access and intrusion authorizations. With central user management, operators can add, delete and modify intrusion-related user passcodes and authorizations directly in the Access Management System v3 as well as organize users by groups or functionalities. The integrated command and control functionality enables operators to arm and disarm intrusion areas directly in the system's user interface as well as to see their arming status on the system map. This provides operators with a central overview of all access and intrusion states, allowing them to handle intrusion alarms efficiently and remotely.
High level of safety thanks to threat level management
Up to 15 configurable threat levels mean that safety measures can be initiated quickly in critical situations such as fire or an armed attack. The threat level state is implemented by one of three triggers: operator workstation, emergency button, or specially configured “emergency” cards that are presented to a reader. The different threat levels can make all doors open, or all doors blocked, or a mix of some open and some blocked. Individual doors can also have their own security profile and allow only certain cardholders access.
Visitor Management

Effective visitor management goes beyond meeting and greeting visitors who enter the reception area. It must enhance building security, protect facilities and employees, and improve users' and visitors' overall experience. The easy-to-use, browser-based visitor management software offers all the required features to manage and record visits with seamless integration to the Access Management client and access control protocols.
Data Protection & Privacy
To protect against cybercrime and loss of personal data, communication is encrypted at all stages. The software also has trusted digital certificates for mutual authentication between server and client and uses secure design principles such as “secure-by-default” and “principle of least privilege.
Grow with BIS
Further expansion and integration with Building Management software is possible by using Building Integration Access Engine software.
Links
Project References